IBM Security Guardium: The Smart Approach to Data Security
One question every 'security-smart' organization should ask is 'does our security team know where our sensitive data resides, who has access to it or the best way to protect it'?
It is no news that cloud-based technologies help increase agility, competitiveness and innovation. However, the complexity, limited visibility, fragmented controls, and slow reporting they also result to exposes any system to threats and vulnerabilities. In linient situations, these results can be undetected threats or delayed migration to the cloud, and in severe occasions, can involve total migration cancelation or reversal.
A great idea such as adopting strategic technology initiatives can be inhibited if you do not adopt the right tools and resources to mitigate threats or address new compliance requirements.Consequently, a smarter and more adaptive approach is required to protect your critical data wherever it resides.
A range of security solution providers exist in today's marketplace to choose from. HPE for instance provide myriad protection products. Microsoft also provide a range of data safeguarding solutions through Microsoft Purview.
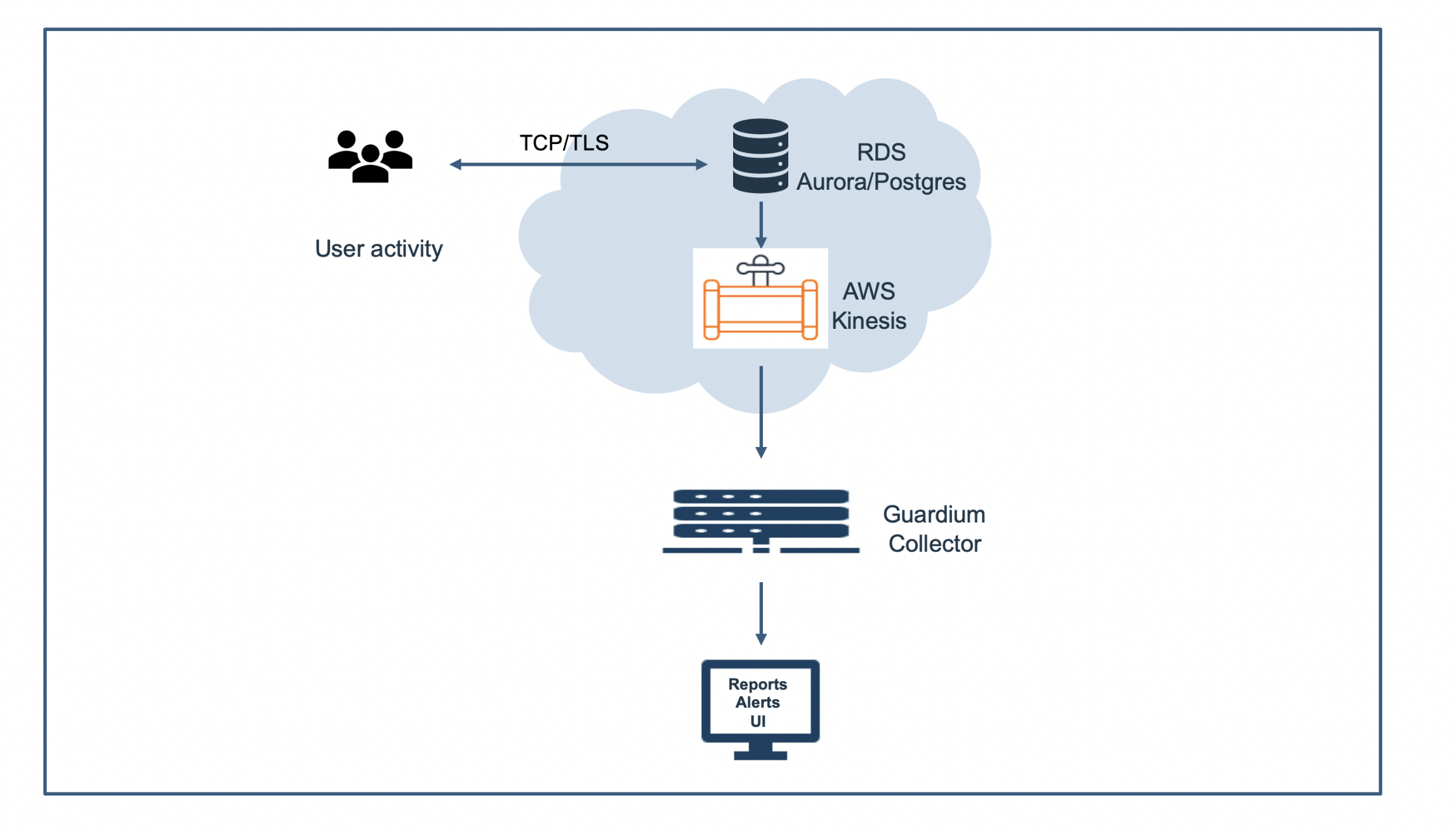
Our focus however on this article is IBM Security Guardium the smart security data protection approach.
Discover the power of IBM Security Guardium for comprehensive data security.
IBM Security Guardium discovers and classifies data, as well as monitors and audits activity to help protect sensitive data across hybrid multi-cloud environments. With Guardium, your security teams can set entitlements and access controls, streamline compliance and get contextual insights and analytics to help detect and block suspicious activity.
TechD provided a list of the things you can do with the IBM Security Guardium platform:
- Automatically discover and classify sensitive data.
- Identify data at risk and get remediation recommendations.
- Monitor access and protect data.
- Simplify security and compliance reporting.
- Encrypt data across environments.
- Use contextual insights and analytics.
- Get a business perspective on data risk.
Strong and approved key management, tokenization, and encryption solutions with Guardium
You need a last line of defence that provides protection as near to your data as feasible while yet allowing authorised users to carry out their duties in the event that your data is compromised. Secure data on-premises, in a single cloud, numerous clouds, or hybrid settings by obscuring it using adaptable encryption technologies.
You can keep control of sensitive data, enforce access controls, and adhere to compliance standards with the aid of file and volume encryption capabilities, tokenisation, application encryption, Teradata encryption, and security key management capabilities.
Scanning for data discovery, classification, and vulnerabilities with Guardium
Manual techniques cannot scale to keep up with the exponential growth of data, comprehend your regulatory exposure, and manage vulnerabilities across your data sources.
To automatically identify the sensitive or regulated data that your organisation has, Guardium provides next-generation data discovery and categorization tools along with thorough vulnerability scanning. Which can help you find database vulnerability exposures and configuration errors and receive remedy advice.
Data security optimization and risk analysis with Guardium.
It is best practice to avoid complexity and enhance data security scalability as you develop data security programs around new requirements, adopt new technologies, and switch to new deployment patterns.
With Guardium you can add enhancements like risk analysis, reporting, and optimization to current data security systems. It'll assist you in streamlining processes, enhancing time to value, and fusing data security data with other solutions to deliver contextual insights.
Download this guide to learn more. Speak to an expert for more information here.