Sparc Systems Limited together with IBM and Interdist Alliances held an event in Lilongwe, Malawi on the 25th September 2019 for a discussion on Border Control and Cybersecurity.
The event, held at the Sunbird Hotel was hosting the Malawian Police to reinforce the importance of CyberSecurity in todays business landscape and to drive the message forward of how IBM Security Systems can further support this very critical business need. These solutions can secure customers data infrastructure and Borderline, Immigration and fraud using i2 and Qradar plus so many more.
Speakers included
*Harry Kasandala, Technical Sales Manager from Sparc Systems,
*Andrew Muwanga, Software and Cloud Business Development Manager and
*Terence Tuwe from IBM
Thank you IBM and Sparc Systems Malawi for the support.
Read More
Topics:
Distribution,
Interdist Alliances,
Cloud,
Compute
With small businesses expanding into the cloud, making an investment in networking is more critical today than ever before. This expansion is driving fundamental change across every IT infrastructure domain. Small Businesses need a network that’s always available, adaptable, fast, reliable and secure.
Read More
Topics:
cisco,
Interdist Alliances,
small business,
discounts,
Meraki,
fast track,
switch,
networking,
promotions,
october,
bundles,
HPE,
migration,
switching,
wireless
In a world where technology is changing our everyday lives, digital transformation tops the strategic agenda in most organizations. Leaders are under tremendous pressure to harness today’s wealth of data and apply it to create new value across the entire organization—all with limited time, skills, and budget. However, building a data-centric organization is no small undertaking.
Read More
Topics:
Kenya,
software,
communication,
Distribution,
Interdist Alliances,
event,
Cloud,
NetApp,
Interdist Conversation,
Partner,
Data,
Digital
Interdist Alliances, in partnership with NetApp, hosted our Data Is The New Oil event at the Victoria Crown Plaza on Thursday, 29th August 2019.
Read More
Topics:
communication,
Distribution,
Interdist Alliances,
Nigeria,
event,
Cloud,
NetApp,
Partner
Commvault has announced a bold and innovative step forward in its partner-first strategy with a new, global partner program that makes it easier and more profitable to do business with Commvault.
The company continues to enable its partners to take a long term and financially beneficial journey together while delivering the industry’s leading data software solutions to customers. The new tools and capabilities available through the Partner Advantage program are designed to help partners accelerate business, expand the path to multiple revenue streams and consistently win more business.
Read More
Topics:
software,
Interdist Alliances,
Interdist Conversation,
Partner,
Advantage Program,
Commvault
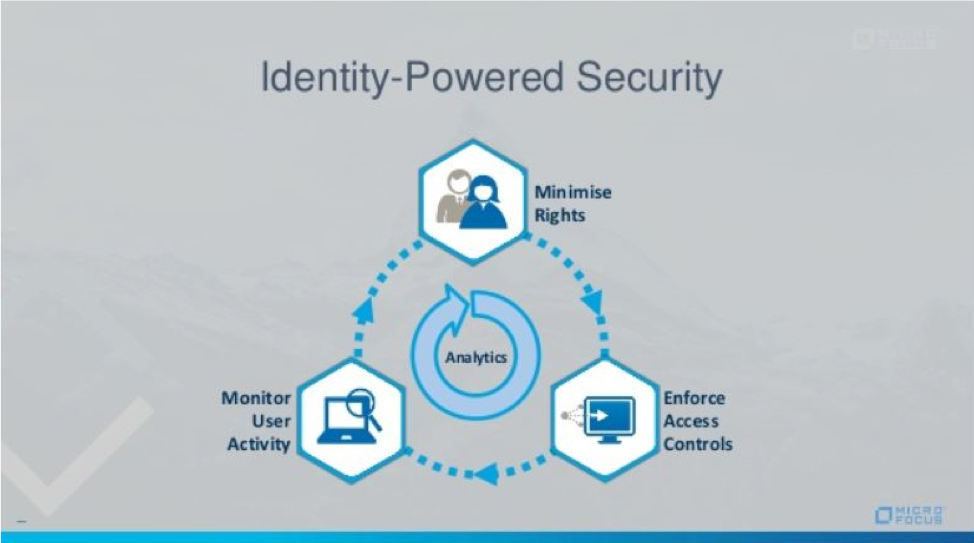
Identity and Access Management (IAM)
With the annual costs of damage associated with cybercrime expected to reach $6 trillion by 2021, businesses need to focus on improving security measures and controlling user access to information. Our Identity and Access Management (IAM) solution by Micro Focus is a critical component of a successful protocol that helps organizations consistently enforce access rights across protected information and help businesses meet regulatory mandates with its integrated policies across local, mobile, and cloud environments by solving the following needs for our customers.
- Visibility - This is a big challenge for growing businesses. As more users join a network, more devices become active and new tools are added to support diverse workflows, it becomes difficult to get a handle on who has access to what resources and at what privilege levels throughout the user’s lifecycle. Our identity and access powered security management and sign-on procedures helps businesses achieve the dual goals of greater visibility and smoother user experiences.
- Pinpoint and Eliminate High-Risk Systems - Many businesses are still clinging to legacy systems for which support has long since ceased. Unpatched systems can become sources of breaches and make sensitive information readily available to hackers. Businesses that rely on these systems out of habit or in an attempt to avoid the hassle of upgrading need to take a step back and assess which needs these legacy tools are addressing and how they’re being used in workflows so that suitable replacements can be found. It may be possible to safely continue using systems for which support is still available, but seeking a fresh solution is still preferable because legacy tools often lack the options required for seamless integration into modern systems with diverse access requirements.
- Crack Down on Orphaned Accounts - Active user accounts contain all the information related to a user’s identity and his or her movement within a network, including access privileges. When a user is promoted to another position or leaves the company, these accounts should be removed. However, with the increasing burden on IT professionals and the lack of visibility in most business networks, this often doesn’t happen. Improper deprovisioning of users leads to an accumulation of accounts with no associated users. Known as orphaned accounts, these sets of credentials and provisions are easy targets for hackers inside and outside the network. Logging into an orphaned account makes it possible to launch phishing attacks using apparently legitimate email addresses, make unauthorized changes to the system and steal sensitive data. Fifty-five percent of enterprises fail to revoke the permissions for privileged accounts, which creates an even greater security threat due to the higher levels of access allowed by these accounts.
- Implement of Zero-Trust Security - In most business networks, it is safe to assume no one is trustworthy until proven otherwise. Our “zero trust” model relies on continuous authentication methods in which user behaviors are monitored and risk levels assessed throughout the duration of each session. By taking a dynamic and sophisticated approach, zero trust equips a system to detect aberrant behaviors indicative of a breach. Instead of taking the average 197 days to discover an intrusion into a system, businesses can identify potential threats and launch a proactive response the moment behavioral discrepancies arise. This prevents hackers from gaining free reign once inside a system and can avert the serious consequences associated with extensive breaches.
- Find the Best Software Solution - Every business needs an IAM solution tailored to the specialized needs of its industry in general and its onsite systems in particular. Threats, risk levels and compliance regulations differ according to the unique combination of devices, user access requirements and tools needed to integrate applications with incompatible authentication protocols. The retention of legacy systems adds another element of complexity with its own related concerns. Streamlining workflows and optimizing productivity without sacrificing security are top priorities in our IAM platform, along with scalability to accept the introduction of new systems, applications and devices. IT professionals require an administrative dashboard with analytics tools, straightforward reporting and a high level of visibility to ensure all endpoints can be monitored continuously.
Key Benefits:
- Give users quick and secure access to resources base on need to know basis
- Secure and simple to remember passwords
- Control and monitoring of privileged users
- Strong authentication without restricting productivity
- Access governance for regulatory compliance
- Make it easy to gain access to IT resources
Read More
Topics:
Distribution,
Interdist Alliances,
Cloud,
Compute
Interdist Alliances and Jetlink
Interdist Alliances, in partnership with Jetlink and IBM, hosted an event at the IBM Innovation Centre on Tuesday, 25th June 2019.
Markets experts at the event included Waheed Adeoye, Elochukwu Mofunanya and Chuks Obi discussing a range of subjects ranging from Power9 Accelerated Infrastructure Foundation, Data Driven by storage, IBM API Economy and IBM Cloud Private. IT influencers and decision makers from all over Nigeria attended this event. The impressive guest list made for an interactive and informative session. The sharp growth of the IT sector in this region is a testament of bigger expectation in the future.
For more information on how Interdist Alliances can assist deliver a seamless experience in your business, contact our office :
3rd Floor,
Africa-Re Building,
Plot 1679 Karimu Kotun Street,
Victoria Island,
Lagos, Nigeria
Tel: +234 802 947 1822
Read More
Topics:
Distribution,
Interdist Alliances,
Cloud,
Compute
Interdist Alliances and DataFlex
Interdist Alliances, in partnership with DataFlex and IBM, hosted an event at the IBM Innovation Centre on Thursday, 27th June 2019.
Guests were graced by industry experts, decision-makers and influencer focusing on IBM Solutions with an emphasis on "Speed meet's Simplicity".
Markets experts at the event included Foluso Jibowo, Funmi Alamu, Chuks Obi and Chukwudi Okafor. The main focus was
Power9-Accelerated Infrastructure Foundation, Data Driven By Storage, IBM API Economy and IBM Cloud Private. The discussions were interactive and involved in depth analysis of the each of the solutions presented.
For more information on how Interdist Alliances can assist deliver a seamless experience in your business, contact our office :
3rd Floor,
Africa-Re Building,
Plot 1679 Karimu Kotun Street,
Victoria Island,
Lagos, Nigeria
Tel: +234 802 947 1822
Read More
Topics:
Distribution,
Interdist Alliances,
Cloud,
Compute
Interdist Alliances and ActivEdge
Interdist Alliances, in partnership with ActivEdge and IBM, hosted an event at the IBM Innovation Centre on Wednesday, 26th June 2019.
Guests were graced by industry experts, decision-makers and influencer focusing on IBM Solutions with an emphasis on "Speed meet's Simplicity".
Market experts at the event included an executive welcome note from CEO of ActivEdge, Mr George Aku followed by presentations from Hillary Ugwuanyi from ActivEdge and Waheed Adeoye, Elochukwu Mofunaya and Olukayode Onyinkolade from IBM.
Creating long-lasting partnerships is at the heart of what we do, supporting our partners' success.
For more information on how Interdist Alliances can assist deliver a seamless experience in your business, contact our office :
3rd Floor,
Africa-Re Building,
Plot 1679 Karimu Kotun Street,
Victoria Island,
Lagos, Nigeria
Tel: +234 802 947 1822
Read More
Topics:
Distribution,
Interdist Alliances,
Cloud,
Compute
Oracle, Interdist Alliances and Harel Mallac
Oracle in partnership with Interdist Alliances and Harel Mallac hosted an Executive Breakfast on Wednesday, 26th June 2019 in the land of the thousand hills. Rwanda's accelerated growth towards cloud-based solutions has led to a highly receptive market that is ready to align itself with the latest the industry has to offer.
The event focused on Oracle Cloud, Autonomous Database and Information Security. Key decision makers were invited to the event for more information on leveraging on Cloud Technologies.
Market experts at the event included an executive welcome note from Mr Allison, followed by presentations on Cloud, Information Security and Autonomous Database from Mr Newton and concluded by the General Manager of Harel Mallac, Mr Shateeaum and Interdist Alliances Oracle Pre-Sales Consultant Denis Kioko.
Oracle experts, were also on-hand to offer insight into Oracle solutions. With Oracle Cloud services, companies can conduct their business operations and connect with their customers better than with any other cloud computing platform. This allows companies to give their customers personalised journeys.
For more information on how Oracle Cloud Services can assist deliver a seamless experience in your business, contact our office :
Interdist Alliances,
Block 3, Delta Riverside,
Riverside Drive,
Nairobi, Kenya
Tel: +254 773 145 680
Read More
Topics:
Distribution,
Interdist Alliances,
Oracle,
Cloud,
Compute